In today’s digital world, cybersecurity threats are becoming more sophisticated, posing significant risks to the integrity of financial data. For businesses subject to the Sarbanes-Oxley Act (SOX), especially those focused on SOX 404 compliance, protecting financial information and implementing effective internal controls is essential for regulatory compliance and for preventing cyberattacks. A comprehensive cybersecurity audit is a key component of maintaining SOX compliance, helping ensure that financial data remains secure and that the organization meets all regulatory requirements.
This article outlines the key steps for conducting a cybersecurity audit tailored to SOX compliance and explains how leveraging
SOX Compliance Services can simplify and strengthen this process.
Understanding SOX Compliance and Cybersecurity
The Sarbanes-Oxley Act, enacted in 2002 in response to major corporate scandals, mandates stringent internal controls over financial reporting for all publicly traded companies. SOX requires companies to implement robust systems that ensure the accuracy of financial data, reduce the risk of fraud, and enhance transparency. Cybersecurity is a critical aspect of SOX compliance, as protecting sensitive financial information from unauthorized access and cyber threats is essential for maintaining compliance.
A SOX cybersecurity audit assesses an organization’s IT infrastructure, internal controls, and data protection mechanisms to ensure they align with SOX requirements.
Steps to Conduct a Cybersecurity Audit for SOX Compliance
Identify Financial Data at Risk
Identify critical financial data, such as financial statements and customer information, to focus protection efforts. Determine where this data is stored and who has access to it.
Evaluate Internal Controls
Review and test internal controls, such as user access management and encryption, to ensure they are effective in protecting financial data.
Assess IT Security Policies
Ensure that IT security policies—including data access, network security, and incident response—align with SOX standards and are well-documented.
Conduct Risk Assessments
Evaluate vulnerabilities that could impact financial data, including risks like hacking, insider threats, and system failures.
Test Controls and Systems
Perform vulnerability assessments and penetration testing on internal controls and IT systems to confirm their resilience against cyber threats.
Ensure Compliance Documentation
Maintain organized documentation of cybersecurity policies, risk assessments, and control testing for external auditors.
Implement Continuous Monitoring
Establish continuous monitoring systems, like EagleEye365 Continuous Control Monitoring, to track real-time threats and ensure ongoing compliance.
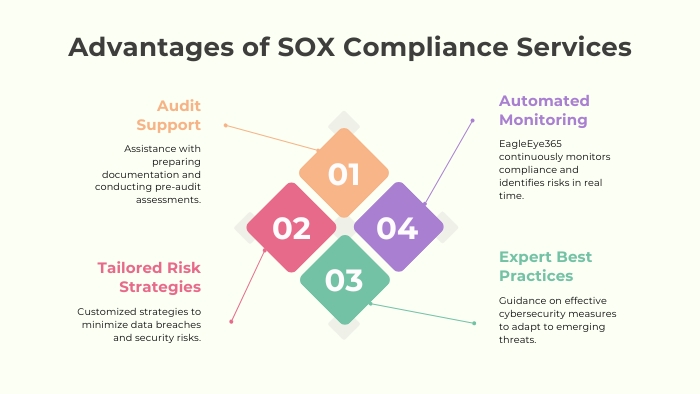
Benefits of SOX Regulatory Compliance Services
Given the complexity and scope of SOX compliance, many organizations choose to engage SOX Regulatory Compliance Services to help manage their cybersecurity and compliance efforts. These services provide specialized expertise and tools to streamline the compliance process, offering benefits such as:
Automated Compliance Monitoring
Compliance services often include the EagleEye365 automation tool, which continuously monitors internal controls and identifies potential risks or instances of non-compliance in real time.
Audit Preparation Support
SOX Regulatory Compliance Services assist in preparing for external audits by ensuring all necessary documentation is in place and by conducting pre-audit assessments to identify areas of concern before auditors arrive.
Risk Mitigation Strategies
Working with regulatory compliance experts enables companies to implement advanced risk mitigation strategies tailored to their specific needs, reducing the likelihood of data breaches or security lapses.
Guidance on Best Practices
SOX compliance services offer expert guidance on cybersecurity best practices, helping businesses stay ahead of emerging threats and regulatory changes. For instance, they may recommend data loss prevention policies to ensure that sensitive financial information is effectively safeguarded.
Leveraging SOX Regulatory Compliance Services allows businesses to focus on core operations while ensuring regulatory compliance and financial data protection against cyber threats.
Conclusion
Conducting a cybersecurity audit for SOX compliance is critical for ensuring that an organization’s financial data remains secure and protected from cyber threats. By identifying key financial data, assessing internal controls, reviewing IT security policies, and testing for vulnerabilities, businesses can meet SOX’s stringent requirements, particularly SOX 404 compliance. Continuous monitoring and proper documentation further reinforce long-term compliance.
For organizations navigating SOX compliance complexities, SOX Regulatory Compliance Services offer invaluable support, providing the tools and expertise needed to streamline the audit process, mitigate risks, and ensure full compliance with regulatory standards. By leveraging these services, companies can protect their financial data, reduce the risk of cyberattacks, and maintain the integrity of their financial reporting.


