Cyber Security Monitoring
Gladius enables you to
The problem
If you use cybersecurity tools from multiple vendors that aren’t integrated, you’re vulnerable in two ways:
Tactical (day-to-day monitoring)
You can add and edit content using the module content settings. It is also possible to style aspects of the content and apply custom CSS using the same settings option.

Strategic (long-term monitoring)
It can get tricky to understand your overall security position and make changes as needed if you don’t look at all your cybersecurity event data in the same place.
Gladius cyber security monitoring allows you to customize your controls and monitoring alerts in ways that most security tools cannot offer.

Solution
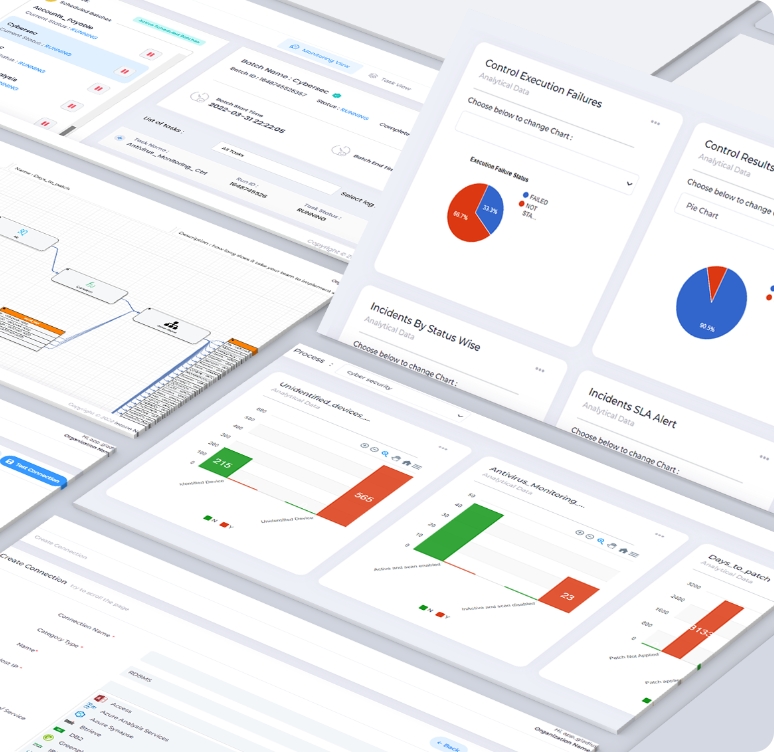
Gladius cyber security monitoring integrates all your security tools into a single real-time platform for continuous control monitoring, with no manual aggregation.
With Gladius, you can design and customize your monitoring of IT security metrics and other performance analytics for better decision-making and faster, more effective responses to cyber threats.
Product
Equips you to custom-craft your security controls.
Monitors endpoints, databases, servers, networks, and data security in real-time from a single platform.
Reduces costs by achieving and proving your compliance faster and with less effort.
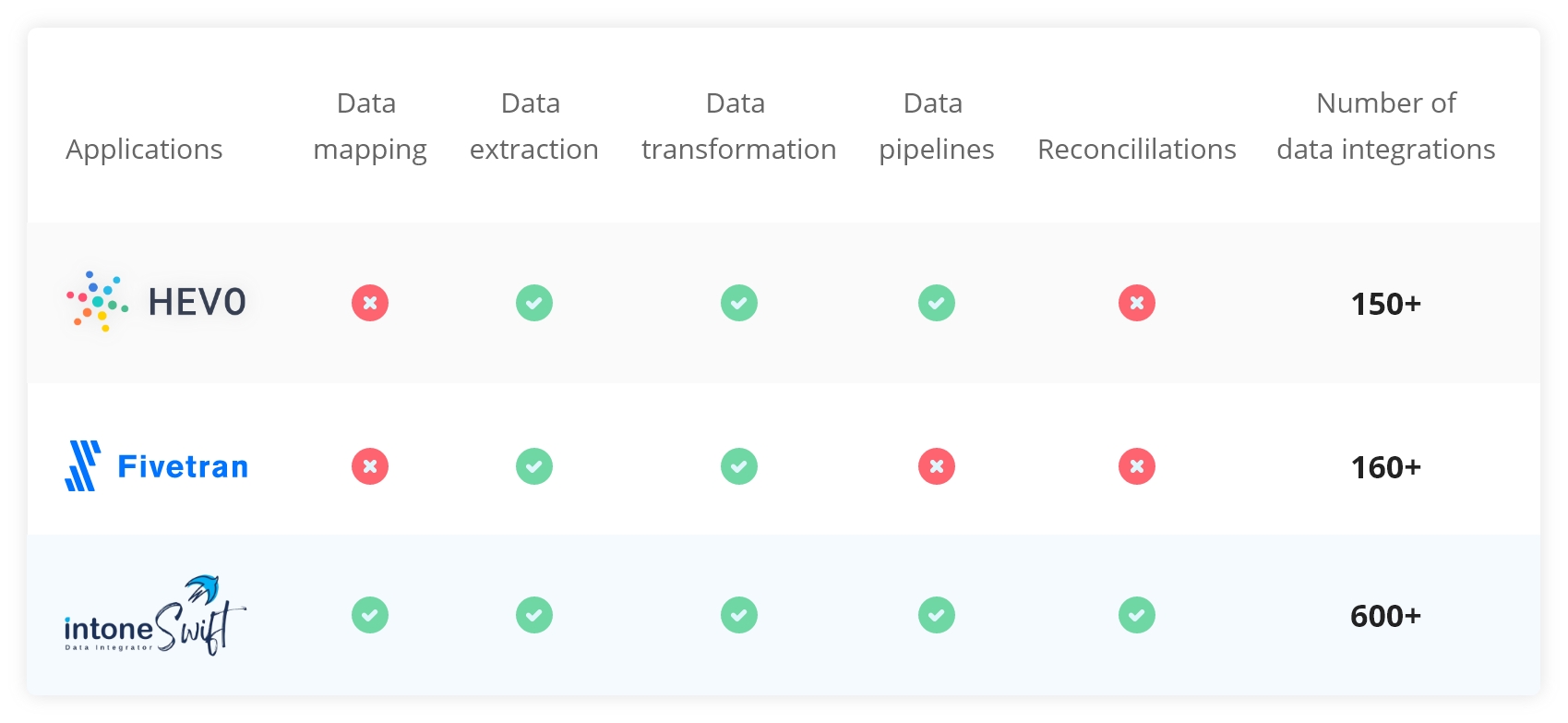
Comes with a centralized IT compliance platform that helps you overcome redundancy between control frameworks, such as SOC, NIST, IASME, COBIT, COSO, TC CYBER, CISQ, FedRAMP, FISMA, and SCAP.